Being proactive in finding security weaknesses within your network helps keep you one step ahead of ever-changing cybersecurity threats
Identify potential attack vectors and protect critical data assets, enabling your organization to proactively strengthen it’s overall security posture.

Gain a comprehensive color-coded report of Critical, High, Medium, and Low vulnerabilities and unsecured protocols for all external live static and dynamic IPs, ports and IP ranges.

Discover all internet facing visible IP devices in your network including security cameras, HVAC systems, forgotten decommissioned servers, etc.

Assists in planning for the risks and benefits of optimizing your security investments and how to roll out your perimeter defense upgrades.
First, we start by planning and defining the scope of your assessment. This involves:

Next, we dive into conducting the actual vulnerability scan to identify potential security threats and weaknesses. We:
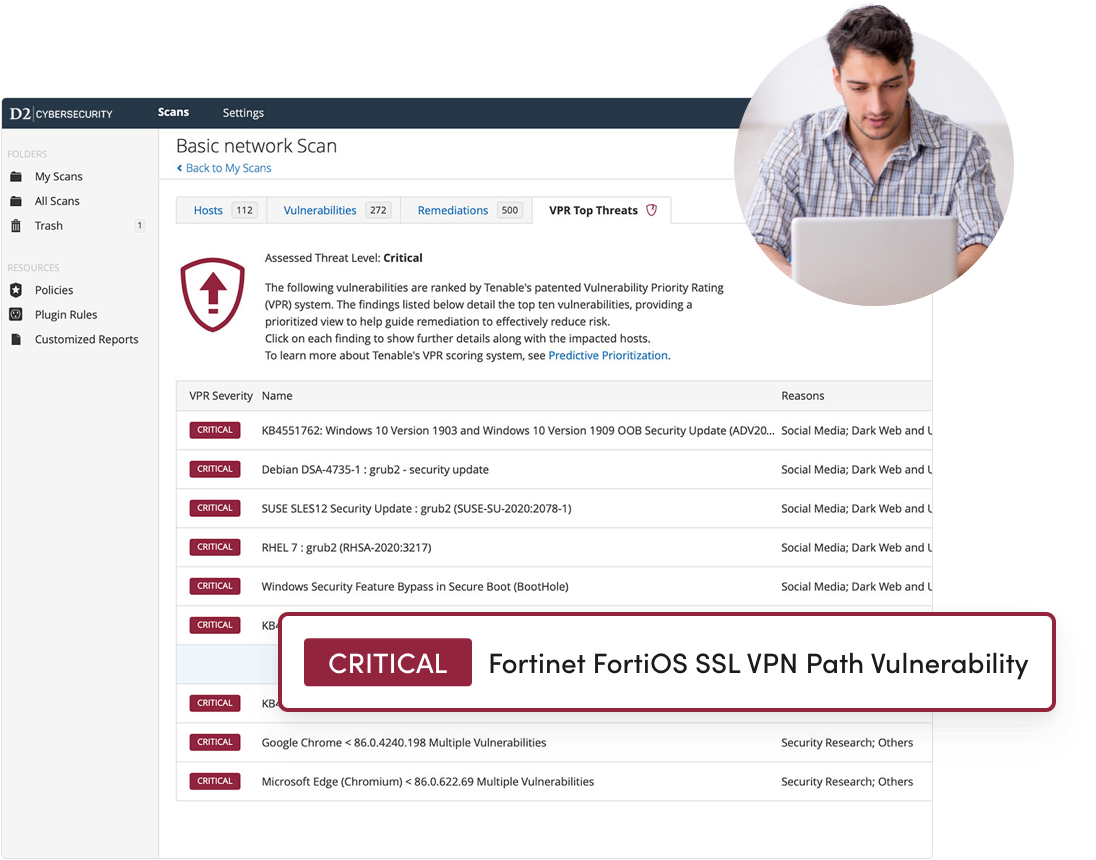
Once vulnerabilities are identified, we analyze, evaluate, and prioritize them meticulously. This involves:
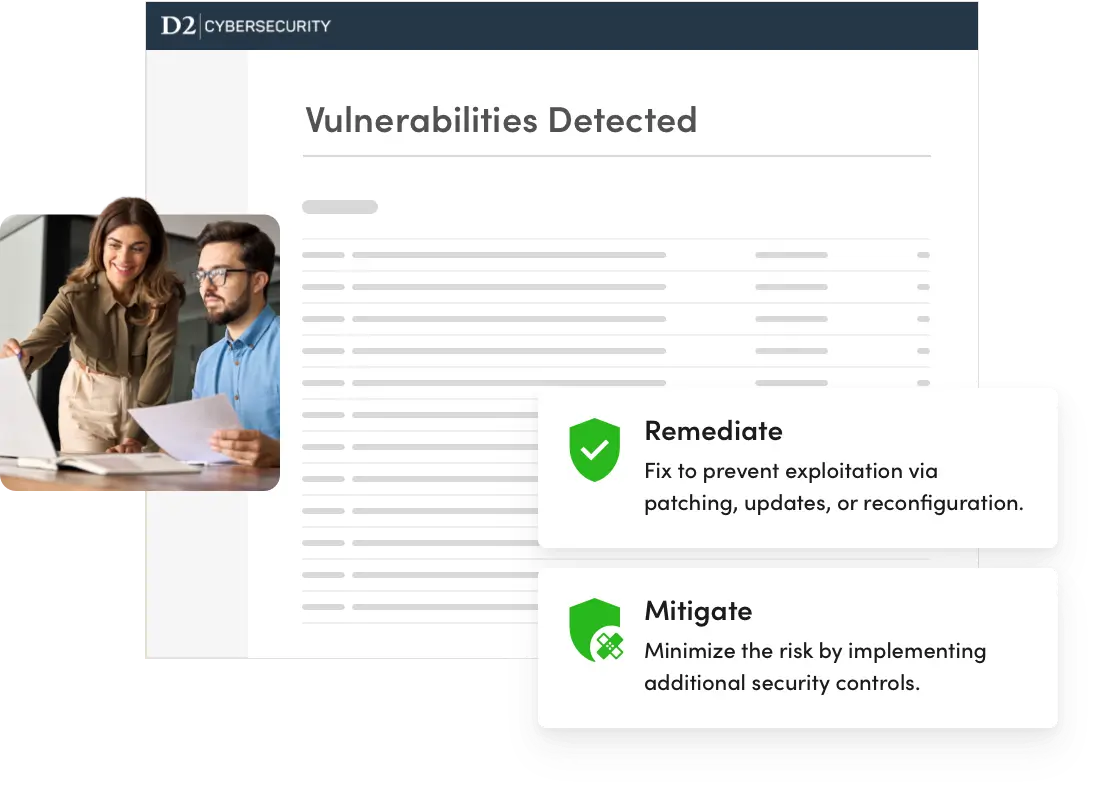
Finally, our D2 security team experts will convene to determine if mitigation or remediation is the best approach for each vulnerability identified.

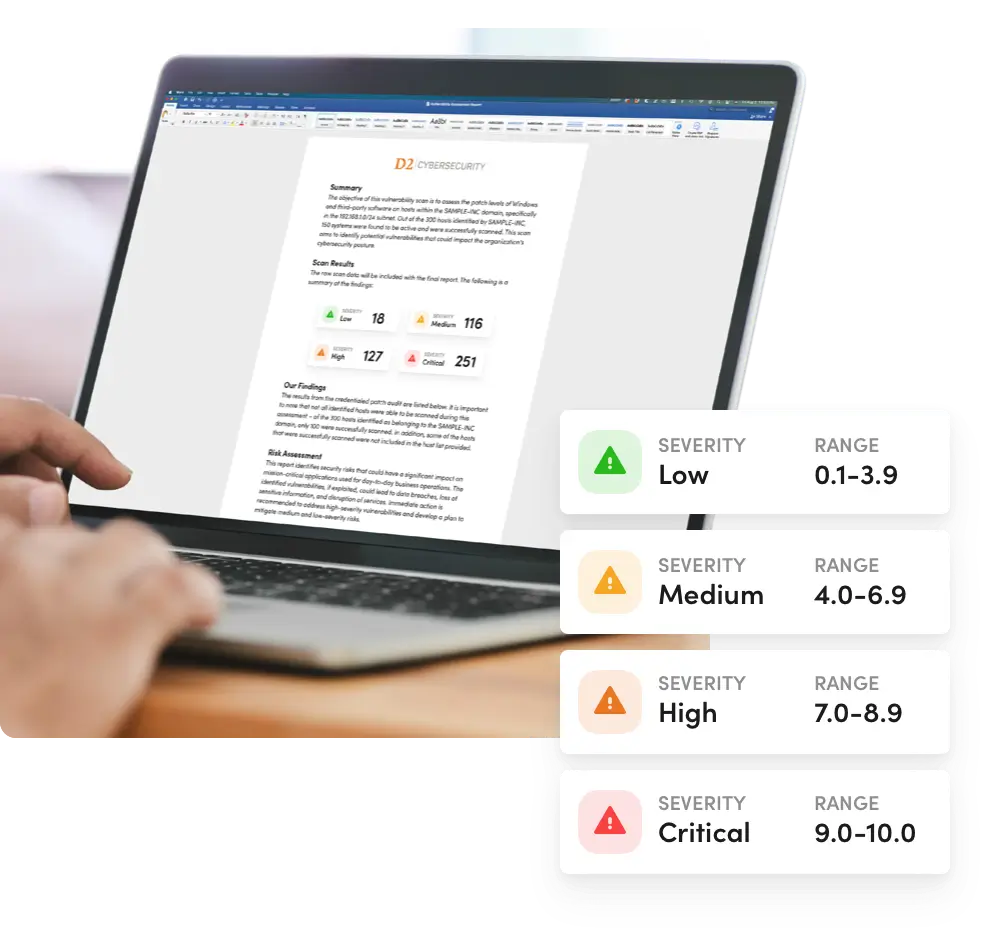
Our advanced scanning technologies and regularly updated threat database, provide clear risk assessments.

Our certified team of experts apply modern ethical hacking techniques to enhance your data security.

Access your detailed vulnerability reports anytime through our easy-to-use portal for quick insights.
Take the first step toward protecting your organization’s private information by contacting us today.
D2 Cybersecurity All rights reserved Privacy Policy