Your organization is unique, and so are its cyber risks. We identify and address these risks with tailored, proactive strategies, ensuring your resilience against any challenge.
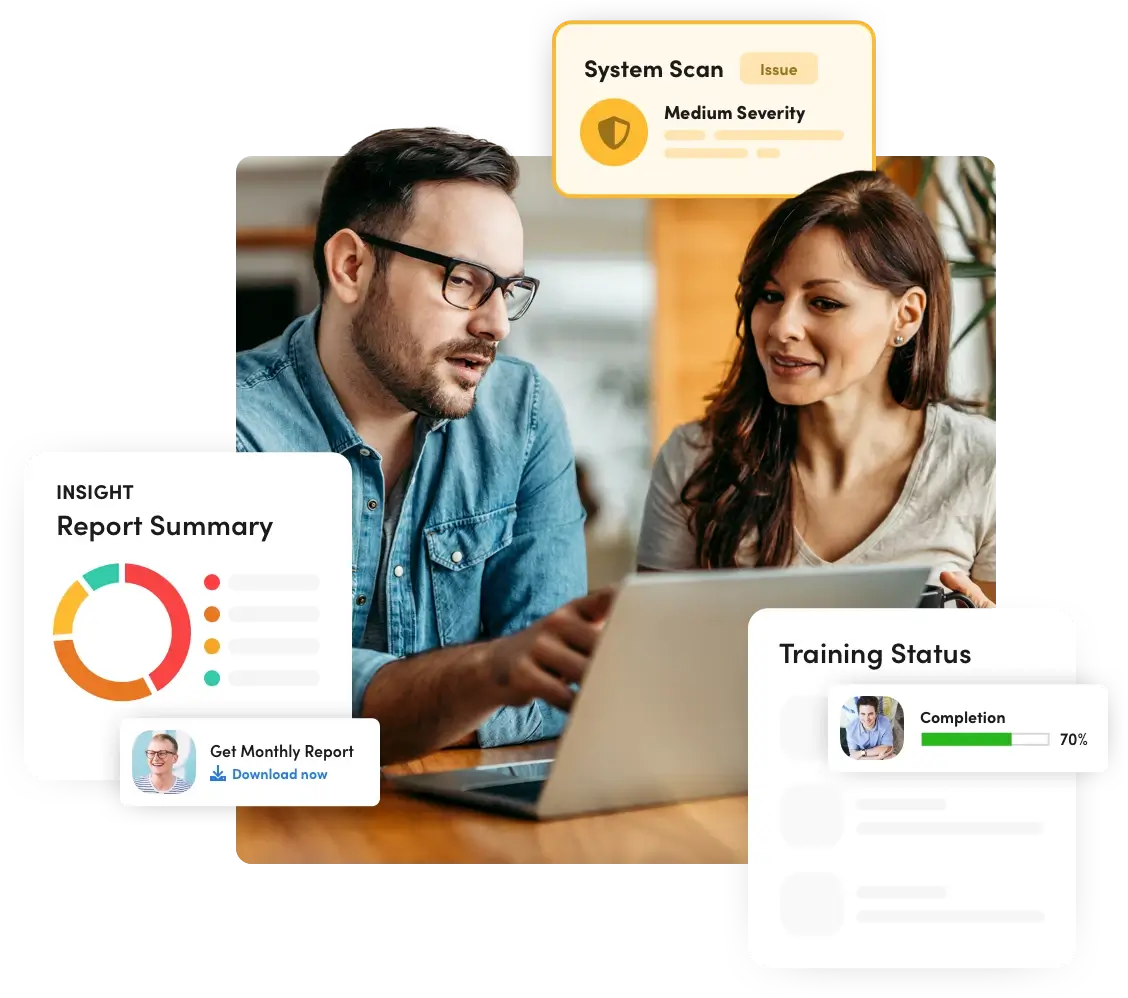






D2’s hands-on administration & guidance elevates group-wide cyber risk compliance.

Monitor your group’s cybersecurity training and phishing performance in real-time to proactively address progress.
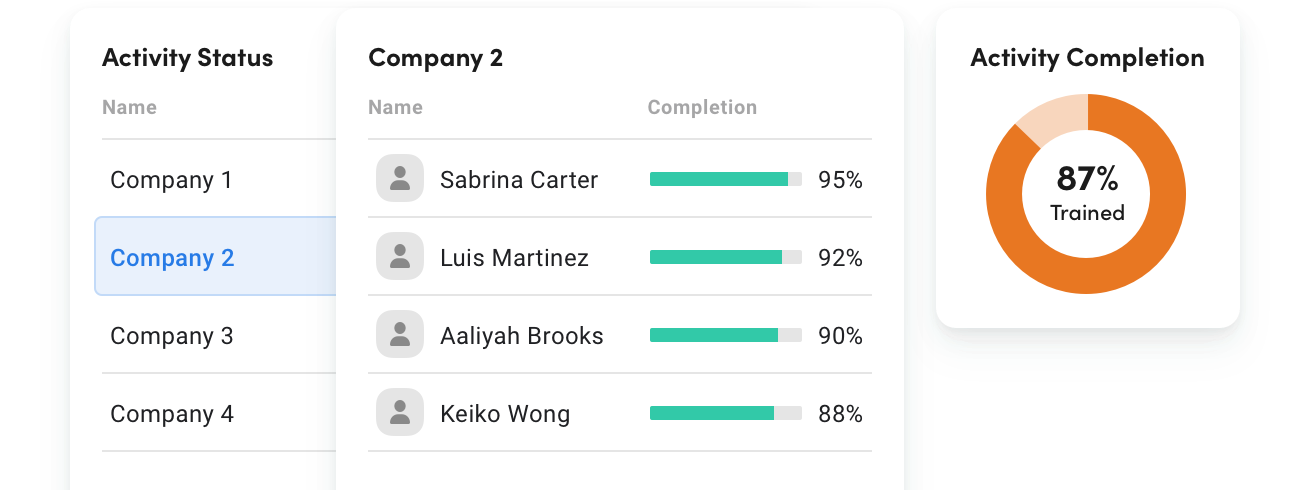
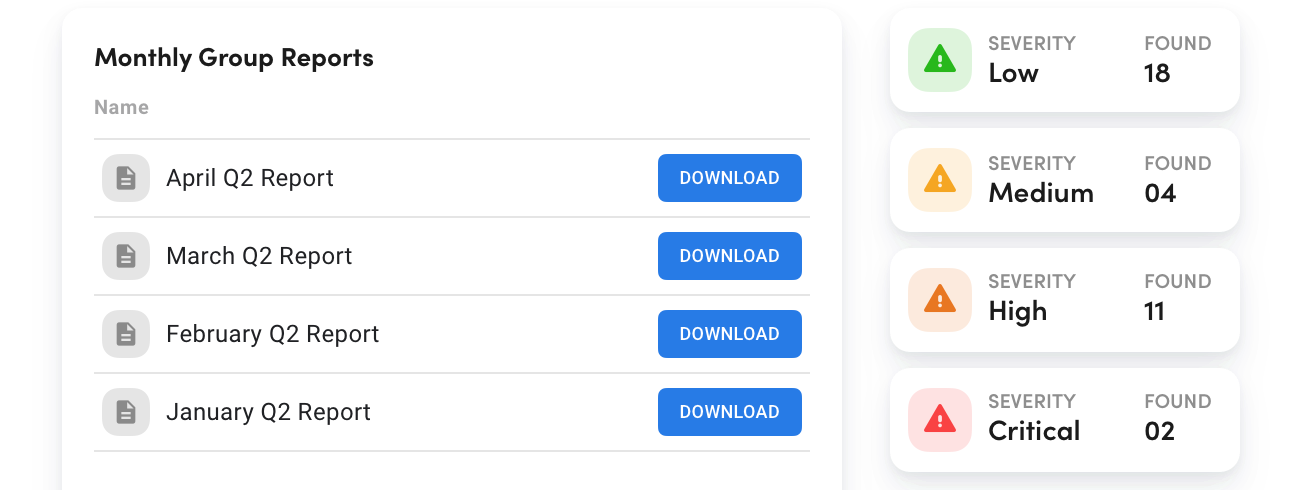
Access on-demand reports for instant overviews of your organization’s cyber status at both group and individual levels.
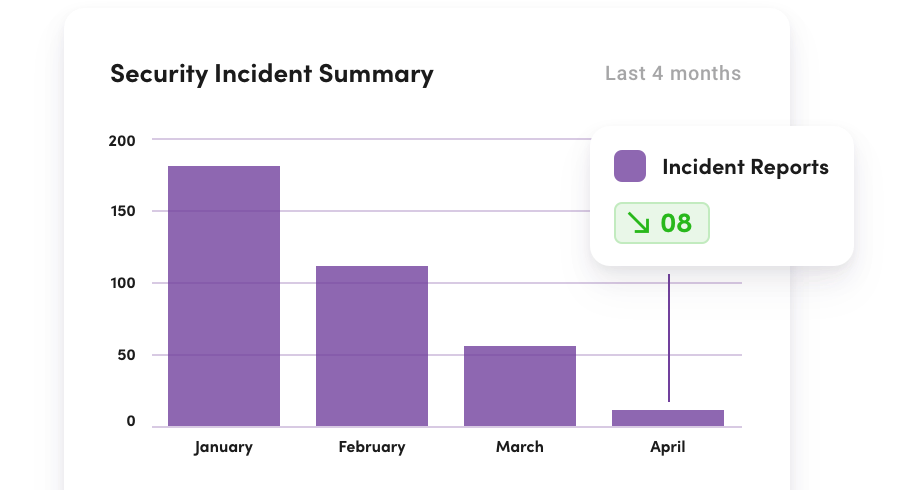
Reduce security incidents to save money, avoid disruptions, and achieve a strong ROI.

Protect whats most important, your staff and students
Secure your school →

Ensure the security and integrity of your systems and data Safeguard your systems →

Lower insurance premiums & protect private information Reduce risk, save money →

Implement security protocols to thwart cyber threats Shield your business →
D2’s cybersecurity risk management services are designed to integrate seamlessly, maximizing the effectiveness of your cyber defenses. As a full-service partner, we collaborate with you to develop a tailored strategy that addresses the technology, people, and processes unique to your organization.
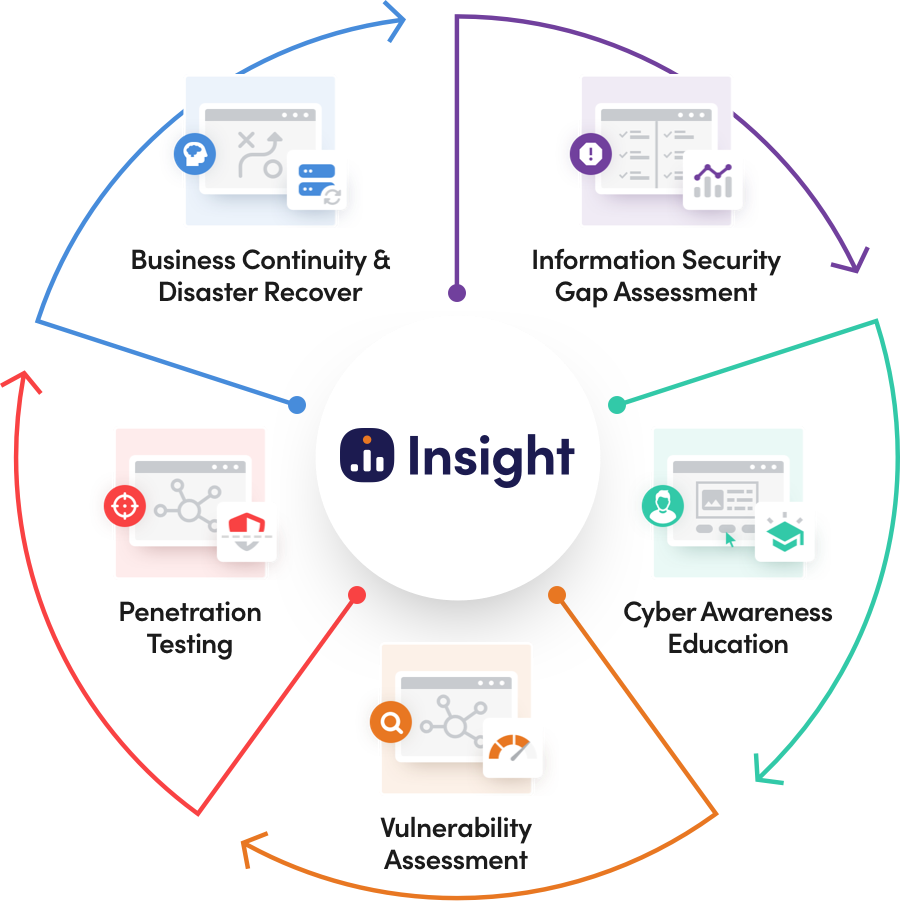

Our security experts will use state-of-the-art tools and techniques to analyze your network for security vulnerabilities, so we can tailor a solution to your organization’s specific needs


The foundation of cybersecurity is education. Our interactive training courses and targeted phishing exercises teach your staff how to protect your network from cyber-attacks.


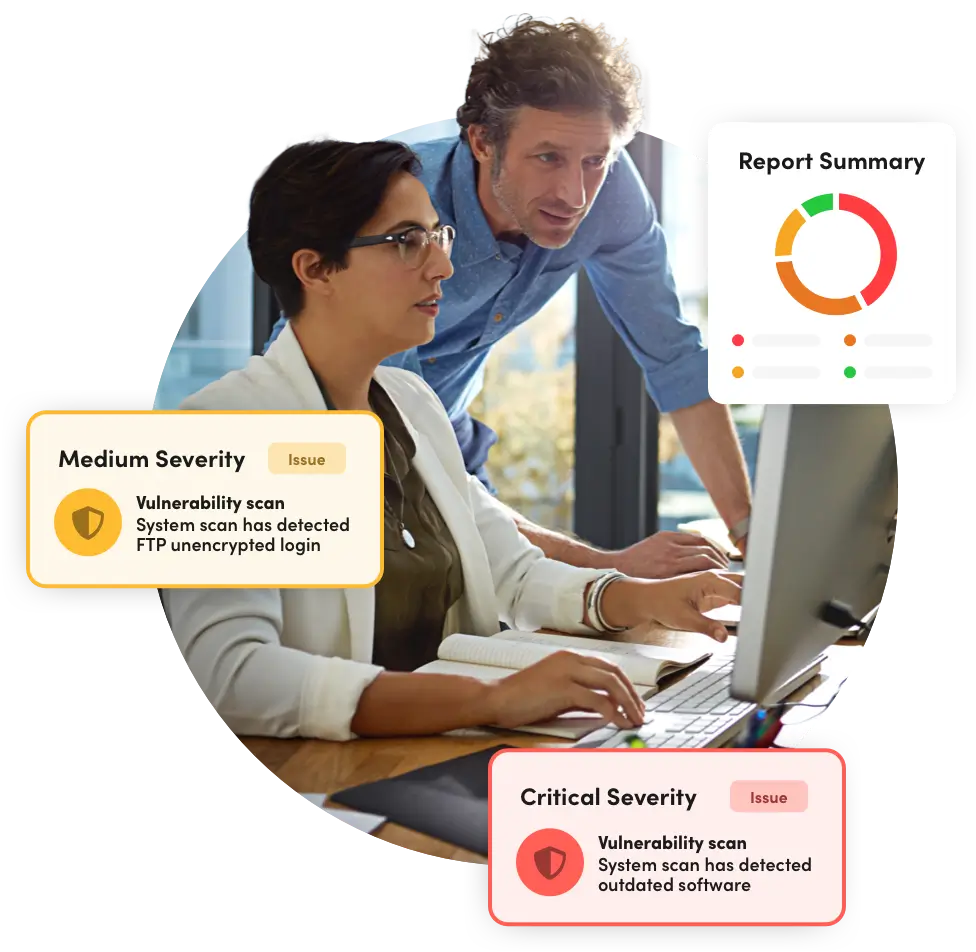
Identify, quantify, prioritize, and receive suggested remediation steps for any vulnerabilities detected in both the internal and external facing systems on your network.

Assess your organization’s current security posture against a simulated cyber-attack. Identify exploitable security flaws within your system and learn how to fix them.


Identify and prioritize recovery strategies for each of your organization’s functions. Establish effective remediation plans based on your business and operational objectives.










Take the first step toward protecting your organization’s private information by contacting us today.
D2 Cybersecurity All rights reserved Privacy Policy